SIEM Essentials
About Course
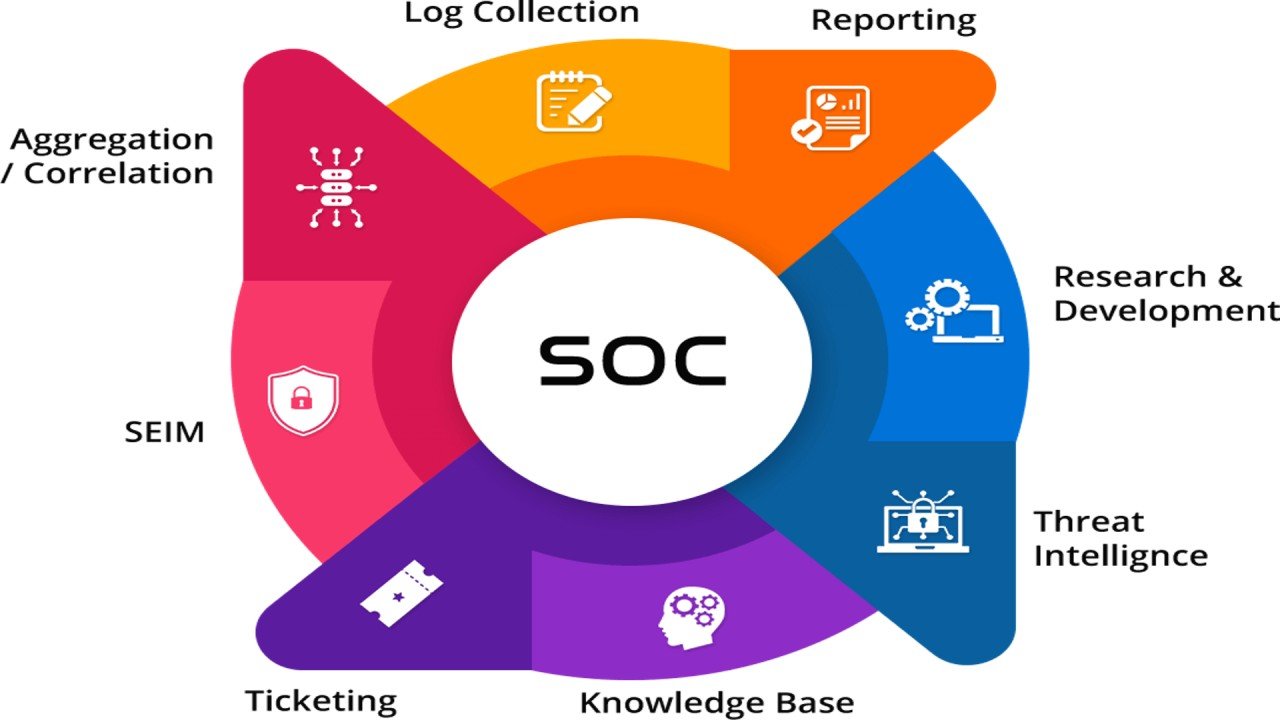
Build a strong foundation in cybersecurity monitoring and threat detection with SIEM Essentials. This course introduces the core concepts, architecture, and operations of Security Information and Event Management (SIEM) systems—key tools used by security teams to detect, investigate, and respond to threats in real time.
Through a combination of theory, hands-on labs, and tool demonstrations (using platforms like Splunk, ELK Stack, or IBM QRadar), you’ll learn how to collect, normalize, and analyze logs from across your network infrastructure. You’ll also explore correlation rules, alerting, dashboards, and incident response workflows.
Whether you’re new to cybersecurity or looking to enhance your SOC capabilities, this course will equip you with essential skills to operate and understand modern SIEM solutions.
🔐 What You’ll Learn:
-
The role of SIEM in modern cybersecurity operations
-
SIEM architecture and core components
-
Log sources: endpoint, network, cloud, application logs
-
Event collection, normalization, and parsing
-
Writing correlation rules and generating alerts
-
Creating dashboards and visualizations
-
Conducting basic threat hunting and incident analysis
-
Integrating threat intelligence with SIEM
-
Overview of popular SIEM tools (e.g., Splunk, QRadar, ELK)
Student Ratings & Reviews
